Canada Has a Cyber Command: What Does this Mean?
A short background and analysis on the creation of CAF Cyber Command
We all may rejoice! It is finally official: On September 26, the Canadian Armed Forces (CAF) Cyber Command (CYBERCOM) was created. This creation was a long time coming, roughly 14 years after the United States CYBERCOM was created and 7 years after the creation of the Cyber Forces. I even advocated for this when I appeared as a witness for the House of Commons Standing Committee on National Defence’s study on the Cyber Defence of Canada in early 2022.
For this article, I will provide a short overview of CAFCYBERCOM, its purpose, basic information on its structure, and why it is so important. In addition, I will give some background and additional insight into how CAF Cyber Command will work and conduct operations based on existing publicly available information.
What is CAFCYBERCOM?
CAFCYBERCOM is Canada’s military organization responsible for cyber operations, including cyber force sustainment, management, and development. CAFCYBERCOM is built upon existing CAF Cyber Forces but expands them into a full command structure that will also include the integration of all of the CAF’s cyber capabilities along with signals intelligence and joint electronic warfare. Signals intelligence refers to the Communications Security Establishment (CSE), which will cooperate with and support the CAF’s cyber operations.
You will sometimes hear the phrase “full spectrum” of cyber operations. Beyond its utility as a term, this effectively means that CAFCYBERCOM will conduct any form of cyber operation, from computer network attack (CNA) to computer network exploit (CNE). However, it remains unclear if only the CSE in CAFCYBERCOM will conduct CNE or if the CAF will conduct both CNA and CNE operations.
This distinction is important because, whereas CNA operations usually aim to cause disruption, CNEs often focus on espionage and stealth. As a result, you often see the military conducting only CNA among NATO countries, while signals intelligence organizations will often do CNE and CNA. This is because the individual mandates of NATO/Western militaries do not always allow espionage-related activities and those related to CNE operations. However, cyber operations do not always neatly fit into these two categories and existing defence intelligence activities covered by crown prerogative likely means that CAF can conduct CNA and CNE operations unless Canadian law changes.
Why is CSE integrated with CAFCYBERCOM?
CSE’s relationship with DND/CAF’s cyber capabilities dates back to the CAF’s initial development of cyber capabilities in the late 1990s and early 2000s. During this time, CSE began to conduct penetration testing of Canadian government networks, including DND/CAF. The CSE has a very close relationship with DND/CAF on cyber operations, mainly in part because CSE is the Government of Canada’s lead agency on cyber and signals intelligence. To put it bluntly, CSE are the experts. They have been pushing DND/CAF and the Government of Canada to do more on cyber for many years and have been developing their capabilities along the way. (Paragraph updated to clarify the timeline of CAF cyber capabilities and CSE penetration testing.)
In 2019, the CSE Act was updated to provide CSE with the mandate to conduct offensive cyber operations (Referred to as active cyber operations in the CSE Act). Included in CSE’s mandate is the ability to provide technical and operational assistance to law enforcement and federal agencies. When they do so, they adopt the same powers and exemptions that the agency supporting does. This allows CSE to work alongside and with the CAF on cyber operations in CAFCYBERCOM and what they have already been applying for existing support.
How will CAFCYBERCOM Be Deployed?
How can the Government of Canada deploy its cyber forces to defend Canada and its allies? This was the question asked by Cabinet and Defence Minister Anita Anand in 2022 when Canada was looking to increase its support to Ukraine and NATO by confronting Russia’s cyber aggression. Two nearly immediate things came out of this.
The Government authorized a hunt-forward operation in Latvia as part of Operation REASSURANCE. Op REASSURANCE is Canada’s NATO-enhanced Forward Presence in Latvia, where they lead the NATO Multinational Battlegroup Latvia.
Hunt forward operations are joint defensive cyber operations conducted between a military and a host military/country (In this case, Canada is hosted by Latvia). The operation serves as both intelligence gathering on the threats targeting the host military/country and a training exercise whereby participants are able to learn from each other and promote the sharing of best practices.
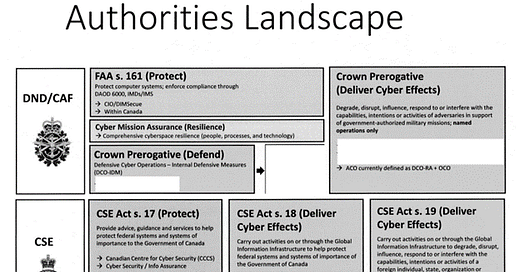
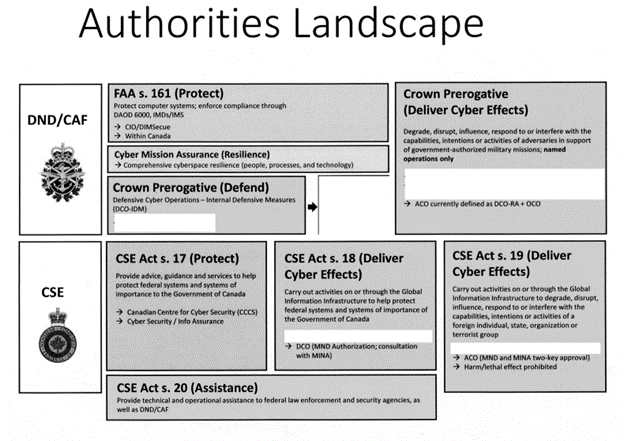
In March 2022, Defence Minister Anita Anand ordered a review of the authorities that the Department of National Defence/CAF and CSE have to conduct cyber operations. Figure B above is a screenshot from this review, obtained by ATIP and found in the Canadian Cyber in Context ATIP archive. What was found is that crown prerogative provides the basis for both defensive and offensive cyber operations, which effectively means that whenever and however the Government of Canada is able to deploy the CAF, it can do so with CAFCYBERCOM.
Ultimately, this means that the CAF must have direct authorization under crown prerogative from the cabinet to conduct offensive operations just like it would to deploy internationally. The authorities landscape above notes that the CAF defines defensive cyber operations—response actions and offensive cyber operations as the same, which makes sense from an authorities and operational perspective, as both involve operations outside CAF networks.
What raises some initial concerns is defensive operations, which occur in the CAF’s networks and require cabinet authorization due to crown prerogative. This would mean that the CAF would need cabinet authorization to conduct operations in their networks, thereby potentially making defence of DND/CAF networks and cyber command and control of defensive operations very cumbersome and difficult. However, this is already addressed in part with DND/CAF’s existing cyber mission assurance mandate that allows DND/CAF to ensure the security of its networks. This is also further strengthened under the Financial Administration Act and multiple Defence Administrative Orders and Directives (DAODs), which are directives from the Government and the Chief of the Defence Staff.
Where is CAFCYBERCOM in DND/CAF’s overall structure?
On 1 May 2024, DND/CAF announced the creation of the Digital Services Group (DSG). DSG combines DND/CAF’s primary ADMs and organizations in charge of the operations and management of digital and cyber capabilities into one unified organization. This is a great development as it helps resolve a longstanding issue of the authorities, responsibilities, and accountability (ARAs) of DND/CAF’s organizations tasked with managing digital and cyber capabilities were overlapping and unclear. The creation of the DSG aligns these organizations to help lead DND/CAF’s digital transformation and continued development of cyber capabilities.
CAFCYBERCOM is led by Major General Dave Yarker, the Cyber Forces Commander, who reports directly to the Chief of the Defense Staff. MGen Yarker was previously the Joint Force Cyber Component Commander, which means that he was overseeing the CAF’s new hunt forward operations in Latvia as part of Canada’s NATO enhanced Forward Presence and the offensive cyber operation that the CAF conducted with CSE.
CAFCYBERCOM is directly administered and supported by the DSG. It’s important to highlight that the DSG includes DND/CAF, both military and government, which allows DND/CAF to consolidate its ability to support digital transformation, cyber operations, and force development of cyber capabilities. Rear Admiral Lou Carosielli is the DSG’s Chief of Staff and is the CAF’s J6 and former Cyber Forces Commander, which situates him as a knowledgeable advocate in DSG to support CAFCYBERCOM.
By reporting directly to the Chief of the Defence Staff, it elevates the role of cyber operations in the CAF by making its commander a two-star general only answerable to the Government’s direct representatives, the Chief of the Defense Staff and Minister and streamlines senior level command and control. This senior level command and control, particularly reducing the steps between cabinet and those in charge of cyber operations, is incredibly important due to how Canada authorizes cyber operations. CSE may only conduct cyber operations with ministerial authorization from the Minister of National Defence, with the Minister of Foreign Affairs consulted on defensive cyber operations and their approval for active cyber operations. For the CAF to conduct the same operations requires cabinet/crown prerogative approval.
This shows that Canada authorizes and approves any form of cyber operation at the most senior levels of government, with the cabinet and the Prime Minister. This reflects the ongoing risk-averse approach to cyber defence that the Government of Canada has taken, but the creation of the DSG and CAFCYBERCOM helps to streamline command and control of cyber operations as the 2019 update to the CSE Act had done. As a result, although Canada has taken a comparatively risk-averse approach, these changes may likely increase confidence in the CAF to conduct cyber operations.
How Will Cooperation on Cyber with CSE Work?
We still do not know much about how and in what ways the CAF and CSE collaborate on cyber operations. Part of the reason for creating CAFCYBERCOM is to formalize and better organize the CAF’s cyber operations with CSE. As a result, we may learn more in the coming years as DND/CAF and work out specifics, but I would not hold out hope for this. For now, we can look at what we know of the CAF’s existing cooperation with CSE on cyber operations and CSE’s similar work with Global Affairs Canada to anticipate likely actions.
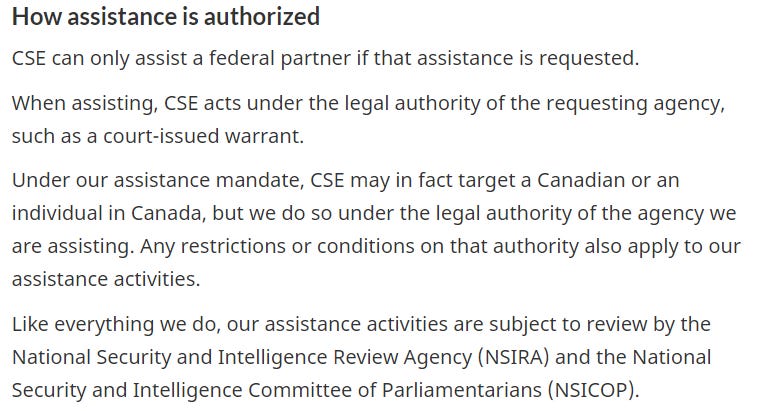
Under CSE’s Technical and Operational Assistance mandate, CSE acts under the same authority and restrictions of the organization they support. As a result, when CSE supports CAF, they are effectively operating as military members of the CAF. This means that CSE bypasses their existing reporting requirements for defensive and active cyber operations, and any cyber operation conducted by CSE in this manner, any offensive cyber operation they support the CAF to conduct is instead reported as “Technical and Operational Assistance.”
So far, the CAF has only conducted one offensive cyber operation, which DND/CAF reported in their 2022-23 DND Departmental Results. However, as far as I am aware, this is entirely voluntary, and there are no strict laws regarding what DND/CAF are supposed to report on about cyber operations.





As a point of clarification, DND's original cyber operations were stood up fully in 1999, vis a vis the Information Protection Centre (IPC), comprising the DND Computer Incident Response Team (DND CIRT) and National Vulnerability Assessment Team (NVAT). I led the former at my retirement in 2001.