A Cyber Defence Review - DND/CAF Departmental Results 2022-2023
Canadian Active Cyber Defense is Finally Active! Government finally admits CAF has conducted offensive cyber operations.
One of the best times every year to understand where and what the Department of National Defence (DND) and Canadian Armed Forces (CAF) are doing is when they release the Departmental Results. Departmental Results are annual reports by Government of Canada departments regarding the performance for the most recently completed fiscal year. The performance is based on the plans, priorities, and objectives set out in the Departmental Plans, which set out expenditure plans, departmental priorities, strategic outcomes, and more. Today I am going to review the cyber defence dimension of the DND/CAF Departmental Results 2022-2023
In other words, Departmental Results tell us how good or bad the department did. Departmental Plans tell us what the department is going to do for the upcoming year. Lucky for us, the DND/CAF Departmental Plan for 2023-2024 is also available, which I will review at a later date.
For the past few years, reading the Departmental results has been the best times to learn about how well, or poor, DND/CAF is doing on cyber. This led to my first Canadian Global Affairs Institute article, Canada’s Active Cyber Defence is Anything But Active. This is why I am happy to say that Canada’s cyber forces are making great strides to improve its capabilities and force posture. So much so that I am not worried about Canada's active cyber defence. However, my concerns are now largely being placed elsewhere, particularly digital infrastructure, cloud, and C4ISR.
Disclaimer: This does not contain all mentions of “cyber” or “digital,” but instead focuses on what I thought was most important or provided the most detailed information.
This paragraph on page 5 of the Departmental Results is a fairly accurate summary of the CAF’s cyber forces.
I have heard that DND/CAF has had some good success in bringing in veterans/reservists who have good cyber skills, particularly offensive cyber skills. A lot of the skilled and good cyber forces Canada got there from experience in industry, and that’s why DND/CAF have been working hard to find ways to keep them to not only use their skills but pass them on to others. This was largely with some more money. Some reading of documents would perhaps hint at flexible and different contracting, but I have yet to see anything definitive about this.
What I have been excited about, and am waiting on some ATIPs to tell me more hopefully, is about DND/CAF learning about how to operate with the Communications Security Establishment (CSE). DND/CAF even had USCYBERCOM and NSA folk come from the United States to meet with DND/CAF and CSE (This is what I specifically ATIPed). DND/CAF have been working on figuring out where and how they operate in this space. Which, from a doctrinal point of view, is honestly a difficult thing to figure out. Ambiguity is the norm in cyberspace, but ambiguity is not something militaries are comfortable with and understandably so.
The most exciting thing only barely hinted at here is that there are now full admissions that the CAF has conducted offensive cyber operations. There have been hints and allusions for about a year or more that the CAF has participated in some potential offensive operations, and the report is now directly telling us this.
The phrase that we have heard since the 2017 defence policy Strong, Secure, Engaged is that Canada was going to take an “assertive posture in cyberspace.” This position has largely been viewed as empty for a few years now, but it now looks like Canada is finally taking greater steps. While CSE has been conducting such operations for years now, it is a critical step when the military begins to do so because it is about setting clear demarcation lines between intelligence or military-based or -led operations.
Both types have different sets of international rules and conduct and particularly allow greater oversight by those involved due to how intelligence and military activities are handled. In addition, the purpose of both are entirely different. While they indeed rely upon one other (or, more realistically, the CAF relies a lot on CSE right now), when CSE conducts a cyber operation, the purposes of this will generally be different from the effects the CAF aims to achieve.
More news began to come out about Canadian hunt forward and other cyber operations in Latvia, Lithuania, and Ukraine. At the time I suggested that it was largely CSE taking on this role. The report seems to prove that I was wrong and it sounds like the CAF led this, with some support from CSE. This is a positive sign in my eyes and an example of the improving capabilities of the CAF Cyber Forces.
Beyond these great advances, we also see a few details about domestic cyber security and defence capacities. It is good to see they have refine their incident response plan, as they will be called on more and more in the future. It has not been an easy few years for the CAF’s incident response team. And of course, they’re always trying to improve service and capabilities with Shared Services Canada, which I hear has long been an issue for DND/CAF.

This is where we see even more explanation of DND/CAF offensive cyber operations. It specifically cites Crown Prerogative and the National Defence Act, which is what you would cite for justified military operations. There is no information about who the target was here, and I’d like to know if we will ever find out as there are a few likely targets. CSE has been conducting more operations against ransomware groups of late. Still, I am unsure if DND/CAF would get in on these operations as targeting criminals may be problematic for Canada from a domestic legal and political point of view.
One thing that should be mentioned and that you may have noticed so far is whenever cyber operations, particularly offensive/active cyber operations, are mentioned, then CSE is there as well. The fact of the matter is that this will remain the case for some time and I am still determining if there will be any DND/CAF offensive cyber operation without CSE support anytime soon. This is for a few reasons.
The first is that DND/CAF is still finding its footing. The report suggests that CAF Cyber Forces have made fantastic strides in developing their capabilities, this growth and development was supported and aided by CSE. CSE already has the expertise and operates in this space, so it becomes an important way to stand up military capabilities to have the two learn from each other and help to promote interoperability. In addition, as mentioned, because CSE has the expertise already, they’re the Canadian experts at offensive cyber operations. DND/CAF will generally want them along because who wouldn’t want that additional support?
Something that I was not expecting was that the CAF is supporting cybersecurity and data exchanges with NATO’s Kosovo Force. The inclusion of this in the report is interesting to note as what will be shown later on, C4ISR and interoperability are apparently turning into a major problem.
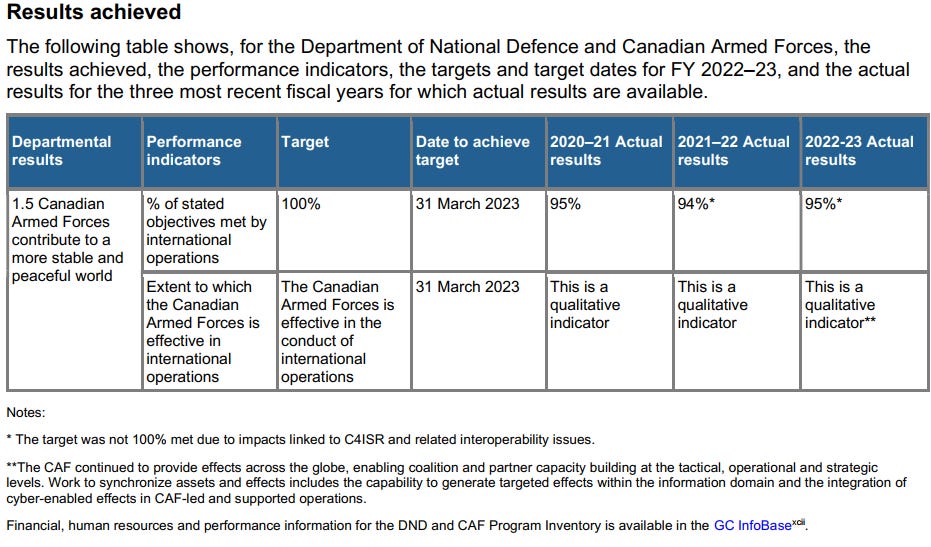
A general rule is that footnotes will always contain the best information, and this graph shows it most of all. CAF achieved 95% of its objectives met by international operations, but they note that it is not 100% because of C4ISR and interoperability issues. While previously, cyber-related objectives contributed to these numbers, it is very notable that C4ISR is cited as the issue.
Command, Control, Communications, Computers, Intelligence, Surveillance and Reconnaissance or C4ISR can mean a lot. However, my general reading and understanding of the state of DND/CAF digitization makes me want to blame the computers and communications portion of C4ISR. Despite this being very broad, being even specific to C4ISR is an improvement over not admitting any faults in the past.
Future Force Design
This is a lot of information and nearly all of it is fantastic. The big highlight out of this is what I only learned a few weeks ago: the CAF is working on a cyber officer trade. I heard a few weeks ago that it was not much of a priority, but they were looking back into it. It sounds like “looking back into it” is conducting a feasibility study, due to be completed in 2024-2025. I would certainly classify that as a lesser priority.
However, that timeline is very interesting because it aligns with the CAF Digital Campaign Plan’s timeline. Although meant to be completed in 2024-2025, that is a feasibility study. Assuming the report says they 100% they should create a cyber officer occupation, it still may be another year or two before we begin to see cyber officers. This is important as 2025 is meant to be when the CAF Digital Campaign Plan is really supposed to kick into high gear, going for a strong centralization of digitization efforts. Cyber officers would help with this, particularly with ensuring the backbone and cyber defense. However, we can comfortably say that there are officers already in the forces that would classify as a cyber officer, so it’s not that they are missing cyber officers. What comes with a cyber officer occupation is the professionalization of the cyber forces, which can help integrate the cyber forces with the rest of the forces and enable the cyber forces to help defend the whole of DND/CAF.
This section also details what I alluded to earlier, which was new flexible contracts and arrangements with cyber operators and additional money to bring in and retain talent. While the force structures still have to be developed or elaborated publicly, they are finally secure in the talent they need and now need to build an institution around that talent. This institutional framework includes figuring out the doctrine on how to use cyber operations, be it incident response and defensive operations or the use of offensive cyber operations in integrated operations. And perhaps in one of my favorite ways that DND/CAF has admitted that they work closely with CSE in cyber, they refer to working with organizations because of the CSE Act, but the only organization they name that they work with is the Canadian Centre for Cyber Security (which is subordinate to CSE).
We also get the first hint of what the C4ISR problems are derived. If we are to take this specific addressing of computer and networking aspects of C4ISR as filling out capabilities that did not exist before, this may show that they are indeed facing a critical networking, data, and communications capabilities deficit to operate with allies. Canada’s entire foreign and defence policy and posture relies upon working with allies, so this should be a deep concern to everyone.
Innovation
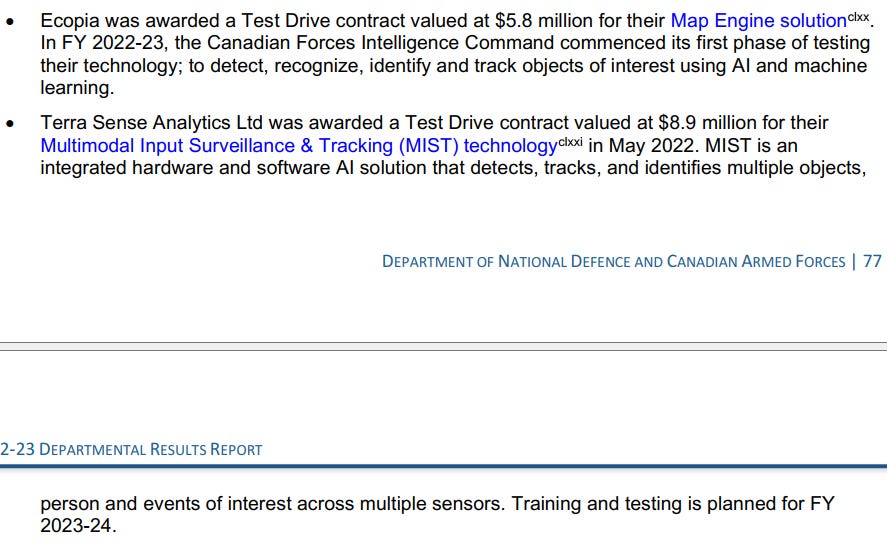
Sapper Labs gets a nice shout out for their IDEaS challenge for what I am told is an EDR platform. Sapper Labs is one of Canada’s leading cyber defence firms, so it is always interesting to see where they pop up.
Sapper Labs is one of many with an interesting IDEaS challenge. DND/CAF have been greatly interested in AI and machine learning applications, already having a lot of experience with Pathfinder in NORAD. The Terra Sense Analytics challenge very much sounds similar to how Pathfinder works, but looking at more than air traffic.
Defence capabilities are designed to meet future threats
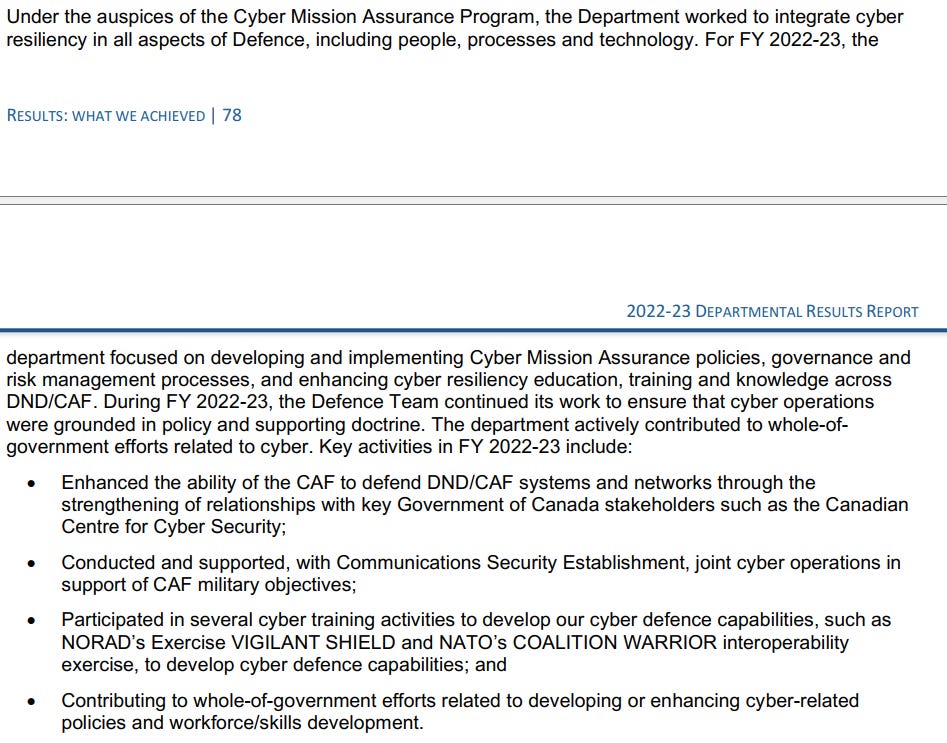
Increasingly, cyber security across DND/CAF is being framed as cyber mission assurance and this is the most high level framing I have seen to date. The CAF for some time has had the Canadian Force Network Operations Centre, but I have heard mixed things about how well it functions or the extent to which they are central to cyber mission assurance efforts. However, this is not to say that DND/CAF does not have good blue team/cyber security folk. Some of the recent performance of CAF cyber operators during international exercises and competitions have begun to show the CAF’s talent. We need to give them the capabilities and institution to do the work.
An upcoming cyber training project?
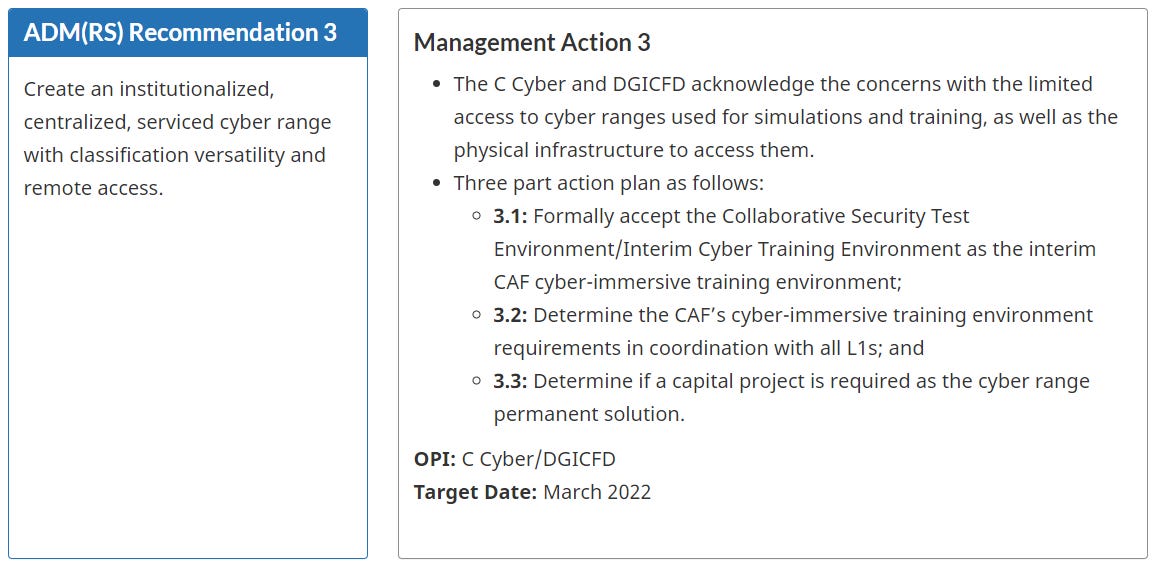
The CAF has been busy with training activities and IDEaS challenges related to cyber and digital capabilities. However, the most exciting part of this section is that it states that an upcoming project on a Cyber Operations Training Ecosystem (CSTE) is awaiting project approval. The best description of CSTE I have seen is that it is a cyber range, but have not seen much details outside of this. I have seen unconfirmed information that may suggest it is nearly 10 years old. Regardless, it was meant as an interim solution from the beginning, so there is a need for a full environment. That means procurement!
Regardless, it appears the CAF wants a different, new cyber range. This is sure to be quite a large procurement opportunity for a Canadian defence organization. Organizations will want to prepare accordingly.
More Cloud!
A big cause of some of the confusion related to my discussion on DND/CAF cloud timelines some weeks ago was if it was protected b or classified cloud which DND was looking to acquire a stopgap capability. Some of the initial confusion was my fault for mixing up classified and protected b, but I have learned is because of mixed messaging from DND internally and externally. Many pointed to the fact that DND/CAF already has cloud capabilities. The reality is that all of the above is correct and it is more classified and protect b that is needed, although it’s predominantly the classified to handle the major data of such programs as the F-35. Having private-sector cloud offerings on a small basis is only a band-aid solution to forces-wide cloud capability to handle massive amounts of classified data in a secure manner.
Some accused me of lying or disinformation because I questioned certain products ability to meet certain security requirements. Still, the problem of all of this is that DND/CAF cloud is a moving target. It’s not about a singular capability of cloud, but about cloud infrastructure and capacity to meet the forces’ needs. Some operators have very serious concerns about certain cloud architectures which have public, well known security issues.
When we talk about cloud as a whole, DND/CAF is just starting to fill this gap. As shown below, DND/CAF have made great improvements by securing the ability to support multiple cloud service providers for Protected B.
There needs to be more to handle everything planned in the CAF Digital Campaign Plan, which stresses a need for a secure and classified cloud, and a shift to a system-centric design. The initial access to cloud services is just a stepping stone and shows that the adoption of such capabilities needs to be balanced across DND/CAF. Having individual shops or groups in DND/CAF that have some cloud access is not a secure, classified cloud capable of handling massive data intensive operations.
I argue that cloud is the foundation for digital transformation and modernization of the forces, but it is one piece of the whole picture. I will not go into deep detail on this, but the page above shows what I mean by just one piece of a whole picture. We traditionally view physical items, cables, buildings, and roads when we think of infrastructure, but increasingly cloud must be regarded as critical infrastructure as opposed to a tertiary capability.
Overall, this should be viewed positively and in the view of digital modernization. There is a significant push to replace analog with digital overall, including adopting digital processes to replace analog. The aim is for everyone to get started in digital modernization and “become digital” in the lead up to 2025. This is all leading towards 2025 because that is when the CAF Digital Campaign Plan fully begins to take over. In particular, is a centralized approach to digital modernization centred around the Digital Transformation Office and the ADM CIO.
I mention all of this because as DND/CAF moves from analog to digital, they will increasingly move away from hardware-defined capabilities and towards software-defined capabilities. Along with this broad adoption of digital and cyber comes greater opportunities to sell to the CAF. While we tend to focus on the large capital projects, much of the money spent is not on these capital projects, but exists as smaller contracts to fill certain operating requirements.
This part begins to show some details on enterprise security solutions revolving around C4ISR, which makes this a particularly important section in light of the stated C4ISR problems. While a lot of this is great, by looking closely you begin to see some gaps. The zero-trust architecture Secure Tailored Solution is only a proof-of-concept capability, which is meant to set the stage for a full procurement of such a capability. The other projects listed are similarly not a full capability. This perhaps starts to show where the problems with C4ISR are, which is that many of these capabilities are not fully operational and potentially can cause difficulties in interoperability if you don’t have reliable and secure means of accessing information when in the field.
Main Takeaways
DND/CAF has come a long way in developing its Cyber Forces. While previously there seemed to be moving backward, I can now say I am quite optimistic about the direction of the CAF’s Cyber Forces. I hope to start seeing more details about force structures in the coming year.
This progress can also directly translate to upcoming projects identified throughout. A summary of major projects to look out for:
A replacement for the CSTE. While details remain limited, DND/CAF looks to be soon looking to start a project to procure a permanent cyber range. This will be a great procurement vehicle and opportunity for Canadian industry.
A major project for a Secure Tailored Solution to securely access classified networks from remote locations. Although the descriptions of this lends to an individual project, this may be part of a larger Secure Tailored Solution project.
C4ISR deficiencies are contributing to an inability to fully meet international objectives and obligations. Not much is given to how or why this is the case, which is also very much a qualitative measurement. However, the fact they are specifically saying it is C4ISR may mean a few things. They are being upfront and honest about the problem they are facing, which is great. However, C4ISR is a very broad category, so we can’t know the specifics for certain. There is also a chance that C4ISR was specifically chosen because it is such a broad category, but I am inclined to think this is not the case.
For all you SMEs out there, there are a lot of opportunities coming up for you! DND/CAF digital modernization under the CAF Digital Campaign plan is ambitious, which means they will be looking for support and to figure out how to fit their needs. As the CAF Digital Campaign Plan takes off and software-defined capabilities have become the norm, this is likely to increase opportunities for Canadian industry